|
|
 |
|||||||







STEM Information Assurance, Information Security and Digital Forensics (IT)
2008 Howard CountyStarlogo |
 |
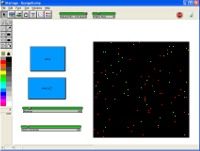
Starlogo Assignment [Word ... PDF]
- You have already examined how groups of things are affected by simple behaviors. Information technology today is flooded by talk of cybersecurity and viruses. But why do they spread so quickly. Let’s model some simple behavior to see how it all works.
- You will design the final model yourself (in groups), but here are some ideas.
- You need at least two types of “things” – they can be either turtles or patches – you decide. I would go with at least computers and viruses.
- You can make the simulation more complicated based on your understanding of computers. For example, you might add servers that have tighter security, or hackers who can get in to things with more protection.
- Think about how you are going to model the items. Some things to think about:
- Computers and servers will upgrade their security periodically. Some may use a fixed schedule; some may only update as new viruses arise. For example, virus software may be updated daily, but windows security fixes may not be installed automatically on an “enterprise” level system. Large companies may need to do their own testing before installing it.
- Viruses exploit different types of vulnerabilities, some may use email/attachments, some may connect through the web.
- Viruses get updated to take advantage of new vulnerabilities.
- Hackers may make more sophisticated attacks at systems and will need higher levels of security.
- Turtles can be different “breeds”. Look at the commands, set-breed, create-breed, breed.
- You can assign variables to turtles and patches. See http://education.mit.edu/starlogodoc/category_command.php?cat_id=10
- Your viruses may move randomly around the screen until they hit a computer, or you can draw connections between them that keep them in fixed paths.
Much as in the tutorial, think about what things you want to happen first, then think about all the individual steps that might happen. (upgrade virus protection, install firewall, upgrade operating system, infect computer (if not protected), multiply virus, crash computer, fix computer, etc.)
|
George |
 |
 |
 |
 |
 |
 |
 |
 |
 |
||
| Educational Technology Policy, Research, & Outreach http://www.edtechpolicy.org// dpruitt@umd.edu |
 |
Copyright © 2009 ETPRO |